The Part Nobody Practices
Buying a hardware wallet feels like leveling up. You go from “exchange user” to “self-custody adult.” And for online attacks, that’s a real upgrade: a hardware wallet keeps your private keys off your laptop/phone, so malware can’t simply copy-paste them away.
But here’s the uncomfortable truth: your wallet’s long-term security is mostly an operational problem, not a gadget problem. The device protects you during transactions. The recovery method protects you during life—lost device, broken device, flood, fire, relocation, inheritance, panic, mistakes.
If you already read “Seed Phrase 101,” you’ve got the fundamentals. This article is the next step: a different angle—how failure actually happens in the real world, and how to build a setup that doesn’t collapse the first time reality bumps into it.
A hardware wallet is a “signing tool.” Your backup is the “ownership plan.”
Think of your crypto setup as two systems:
1) Signing system (daily use)
- Hardware wallet + PIN/passphrase
- Great against phishing and remote theft—if you use it correctly.
2) Recovery system (when things go wrong)
- Your seed phrase (usually 12–24 words)
- This is what restores control if the signing system fails.
Most people obsess over the signing system and improvise the recovery system. That’s like installing a bank vault door and then leaving the master key under a flowerpot.
Takeaway: Your setup is only as strong as your backup.
The Confidence Trap: you protect against hackers, then lose to… your kitchen
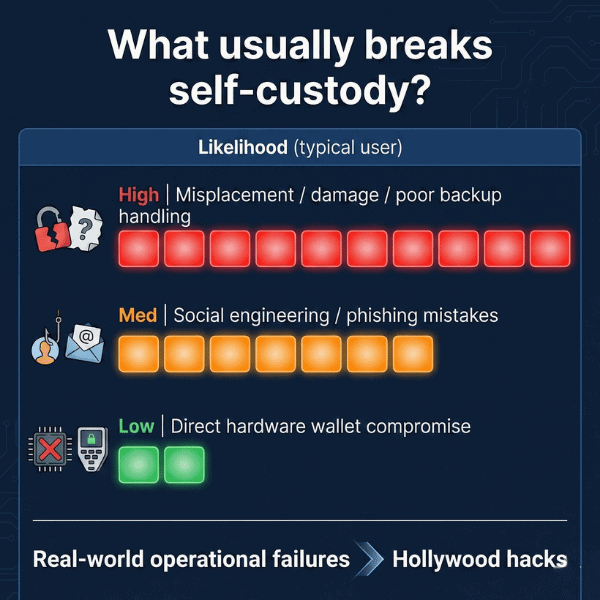
People imagine crypto loss as a Hollywood hack. In practice, many losses are painfully ordinary:
- a move
- a renovation
- a “safe place” that’s too safe
- a spilled drink
- a curious visitor
- a partner cleaning “random papers”
- a device failure at the worst moment
If your recovery depends on a single fragile item in a single location, it’s not security. It’s hope.
Infographic: What usually breaks self-custody?
The silent bypass: when your seed touches a phone, it becomes searchable
A hardware wallet is meant to keep secrets offline. But the seed phrase is often “handled” with online tools:
- photo / screenshot
- notes app
- email draft
- cloud drive
- “encrypted” storage without understanding the tradeoffs
At that moment, your security model quietly changes.
A hardware wallet blocks remote attacks on your keys.
But if an attacker gets your seed phrase—through malware, cloud leaks, backups, synced photos, or compromised accounts—they don’t need your wallet, your PIN, or your permission. They can restore the seed anywhere and drain funds.
Rule of thumb: If your seed exists as pixels or typed text on any internet-connected device, it’s no longer cold.
Paper is offline… but it’s not resilient
Paper is recommended because it’s simple. But it’s also fragile.
- Heat destroys it quickly.
- Water turns it into unreadable mush.
- Ink fades.
- Mold and pests do what mold and pests do.
So if your entire portfolio depends on one paper card surviving decades of unpredictable life, you’re not practicing self-custody. You’re practicing delayed regret.
Chart: Durability mismatch (simple reality check)
| Backup medium | Water | Fire/Heat | Time (decades) | “Found by someone” risk |
| Paper card | Bad | Terrible | Mixed | High (readable) |
| Screenshot / notes | Catastrophic | Doesn’t matter | “Forever online” | Extreme |
| Metal (properly marked) | Strong | Strong | Strong | Lower (can be disguised/encoded) |
The whole-setup test: a quick scorecard
Give yourself a point only if the answer is genuinely “yes.”
Recovery resilience
- I can restore my wallet without any single device (laptop/phone) involved.
- I have at least one backup that survives water + heat + time.
- I have tested recovery once (not “I assume it works”).
Exposure control
- My seed has never been photographed or typed into an online device after setup.
- My backup doesn’t look like a crypto backup to a random person.
- I can explain what happens if a family member finds it.
Continuity
- I have an offsite copy or plan that survives a local disaster.
- I have a plan for inheritance (even a basic one).
If you’re under 6/10, your hardware wallet is doing its job… while your backup strategy is doing interpretive dance.
Actionable tips (that don’t require paranoia)
1) Separate “use” from “recovery”
Your signing tool can travel. Your seed backup should not. Keep recovery boring and stable.
2) Do a recovery drill once
Set aside 20 minutes. Restore on a fresh wallet (or a spare). Confirm addresses. Confidence without testing is cosplay.
3) Avoid readable labels
No “seed phrase,” no “bitcoin,” no “Ledger words.” Treat it like a spare house key: unmarked.
4) Use geographic separation
One backup in one building is a single point of failure. Fire, theft, flood—pick your favorite villain.
5) Upgrade the medium
If you’re serious about holding value for years, use a backup designed for physical reality: metal.
Where KryptoDots fits (without the salesy fog)
KryptoDots is built around a simple idea: make the recovery system survive the real world, and make it less obvious to outsiders. Instead of storing plain words, you encode word indexes into a punched-dot pattern on stainless steel. That gives you durability, plus a stealth advantage if someone stumbles across it.
Takeaway: Your setup is only as strong as your backup.
Fix the weakest link—upgrade the backup.

Leave a Reply